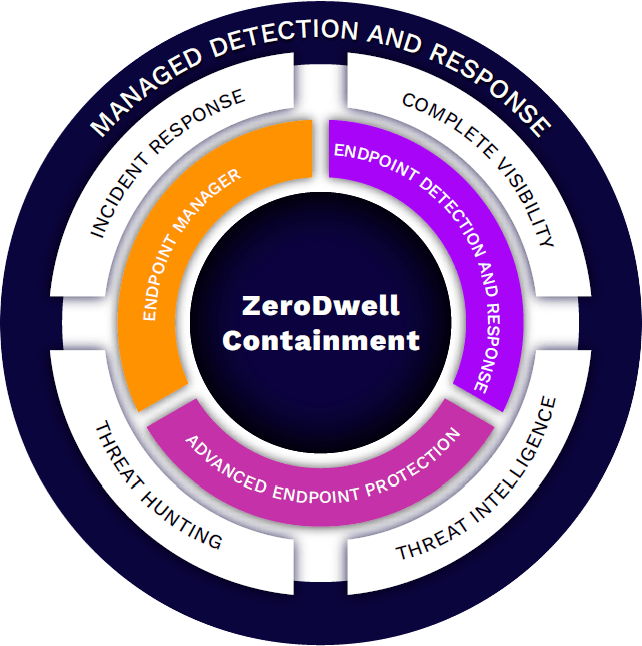
Move Away From Ineffective Detection-First Strategies With Patented Breach Prevention Built For Today’s Challenges!

Our experts closely monitor your environment 24x7x365 and respond regardless of your time zone or location.
offload day-to-day security event triage and analysis so your team can focus on organizational needs
Get high fidelity notifications on file-less attacks,advanced persistent threats and privileage escalation attempts.
Our Verdict Cloud conducts multiple arrays of run-time behavioral analysis against unknown files to provide a verdict of sage quickly and automatically or malicious
Forensic acquisition of digital evidence and detailed timeline analysis for root cause identitication.
Received detailed reports on threat activity affecting your environment,vulnerability management & insight into compliance reporting
| Levels of Service | Xcitium Guided | Xcitium Managed (MDR) | Xcitium Complete (XDR) |
| ✓ Included + Add-on − Not Included | High Fidelity Alert Triage For Endpoints | Managed Detection Response for Endpoints | Extended Detection & Response |
| MANAGED DETECTION & RESPONSE | |||
| Alert Triage & Analysis | ✓ | ✓ | ✓ |
| High Fidelity Threat Notifications | ✓ | ✓ | ✓ |
| Incident Response & Forensics | − | ✓ | ✓ |
| Pro-active Threat Hunting | − | ✓ | ✓ |
| 24/7/365 SOC Services | ✓ | ✓ | ✓ |
| Data Storage for 365 days | − | ✓ | ✓ |
| Live Remediation Support | − | ✓ | ✓ |
Monthly Health Check Meetings | − | ✓ | ✓ |
| NETWORK | CLOUD SECURITY | |||
| x/MDR Network and Cloud | − | + | ✓ |
| SERVICES AND SUPPORT | |||
| Guided Deployment and Health Checks | + | + | + |
| IR Retainer | + | + | + |

100% in protection against 0-day malware attacks, inclusive of web and email threats.
100% in the detection of widespread and prevalent malware discovered in the last 4 weeks.

Xcitium Advanced Endpoint Protection can protect against the unknown file and solves the malware problem

2018 Trust Award Best Managed Security Service
2019 Finalist Threat Intel Technology
4.2 /5 Rating for Endpoint Protection Platform
4.3 /5 Rating for Advanced Endpoint Protection
4.5 /5 Rating for Endpoint Detection and Response

Last test: March 2022 Recent result: 100%
2x | 2022 Excellence Award
Total awards granted: 16 Product of the year: 2021, 2020





